The Best Strategy To Use For Managed Service Solutions
Fully grown MSP's perform upkeep and also feedback solutions using a centralized console that is linked to your IT framework. Rates models for an MSP vary yet usually operate a subscription basis. Continue reading to find out about the fundamentals of utilizing an MSP as well as what to get out of the connection. Buying a complete in-house IT department is quite an undertaking.

There is little interest paid in the direction of proactively checking and also preserving the setting. After all, per hour service firms make their money replying to technical issues. In today's globe, the dangers of bad IT monitoring techniques are severe. Internal IT may have unconfined accessibility to delicate info such as human resources, financials, as well as intellectual building.
An Unbiased View of Collaboration Solutions

If you are considering hiring an MSP, do your research and also make certain that they use the complying with services: While the above-referenced list is not extensive, it gives you a good suggestion as to what you should ask when experiencing the procedure of choosing an IT took care of solution carrier, like F12 (Security Solutions).
A per-incident pricing version charges a cost per ticket, telephone call, or service involvement. Typically, per-incident fees more than as well as over a monthly base charge. All-Inclusive: Complete package choices resemble "complete" getaways. It is a comprehensive all-in-one remedy for every gadget as well as user under a foreseeable price. Like getaway bundles, all-encompassing IT plans have various additions as well as exemptions.
Still, exercise an important mind when searching for a taken care of company in Canada. Make sure to establish if they are a suitable for your organization and also if they dedicate themselves to comprehending sector growths. F12 offers managed IT Solutions across Canada in the following places:.
For your simple look, we have actually separated the handled solutions into main and also second here, according to their significance. End customer services can consist of a wide variety of options, yet they regularly center on the IT helpdesk support channels as well as treatments that a business has established up for its team and also clients (Mobile Working).
The 6-Minute Rule for Security Solutions
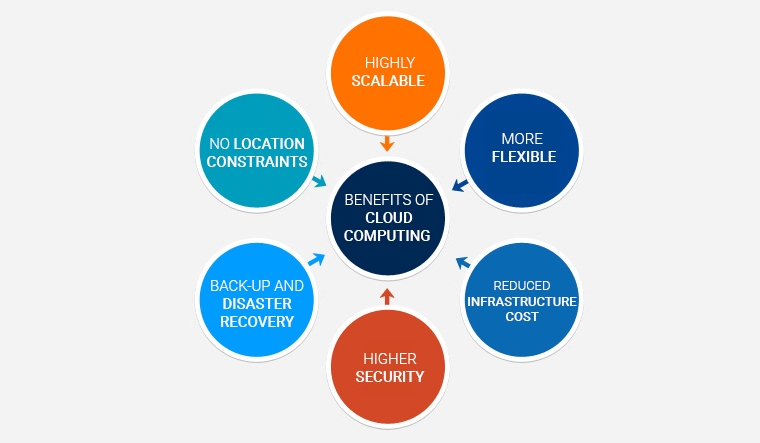
Lots of companies are implementing technology like IT automation, Desktop as a Service, BYOD policies, and much more as end-user expectations and technology both develop. Managed framework solutions need to be thought about when assessing the many managed service groups offered. Consider IT infrastructure as the lifeline of any kind of firm; as important business procedures and also routine procedures become extra electronic, the framework that sustains them needs to perform at its best.
This listing demonstrates the selection of the handled solution market. They do not need the workers or resources to build it themselves; they may hire an MSP to fulfill their needs, whether they are small or big.
Wireless connections will be implemented by an MSP that offers handled cordless and mobile computing. Businesses that lack the funds to buy establishing their very own can take advantage of this service. Organizations can use this service for inner networks too. A range of communication facilities, consisting of Vo, IP (phone over web method), data, as well as video clip, are used by this kind of service.

Some Of Mobile Working
Handled services incorporates a great deal of IT solutions as well as services. Every organization has different IT requires, so some could utilize a Managed Provider for great deals of solutions while others may utilize simply a couple. In any case, took care of services can be a really effective and also economical IT that site method for organizations of any kind of size.
Desktop as a Service is the provision of a full-featured desktop that customers can access from any kind of device and any type of area. Users are guaranteed a protected connection to their work desktop, plus access to all the programs and data they require, any place they are.
Various other employee are granted accessibility to the information and documents they require to do their tasks, without having the ability to access the information they do not need. An IDAM service can also assist with compliance, especially in the age of GDPR. With Handled hosting, your systems and applications are released on the MSPs facilities, which gets rid of the need for up-front costs on servers and also tools.
There are so many subjects to attend to! This listing demonstrates the selection of the taken care of solution market. Businesses will certainly take advantage of having coverage for all elements of their IT, many thanks to this. They don't need the personnel or sources to construct it themselves; they might work with an MSP to satisfy their Read Full Article demands, whether they are tiny or big.
A Biased View of Security Solutions
Wireless connections will be placed in area by an MSP that uses taken care of cordless as well as mobile computing. Companies that lack the funds to invest in establishing their own can gain from this service. Organizations can use this solution for internal networks. A range of interaction frameworks, consisting of Vo, IP (phone over internet procedure), information, and also video clip, are provided by this kind of solution.
Past specialized solutions, team services can also be used to execute support. Every organization has various IT requires, so some might use a Managed Solution Company for great deals of services while others may utilize just a pair. IT approach for organizations of any kind of size.
Mobile working is increasingly common. Whole lots of check over here people currently function from home or on the move, rather than mosting likely to the workplace on a daily basis. Desktop as a Solution is the arrangement of a full-featured desktop that customers can access from any device as well as any area. Individuals are guaranteed a protected connection to their job desktop computer, plus accessibility to all the programs as well as information they need, anywhere they are.
What Does Mobile Working Do?
Various other team members are approved accessibility to the information and documents they need to do their tasks, without being able to access the data they don't require. An IDAM remedy can likewise aid with compliance, especially in the age of GDPR. With Managed hosting, your systems as well as applications are released on the MSPs framework, which removes the requirement for up front spending on web servers and also tools.